Top-notch Security
Robust security features protects your data—letting you focus on things that matter.

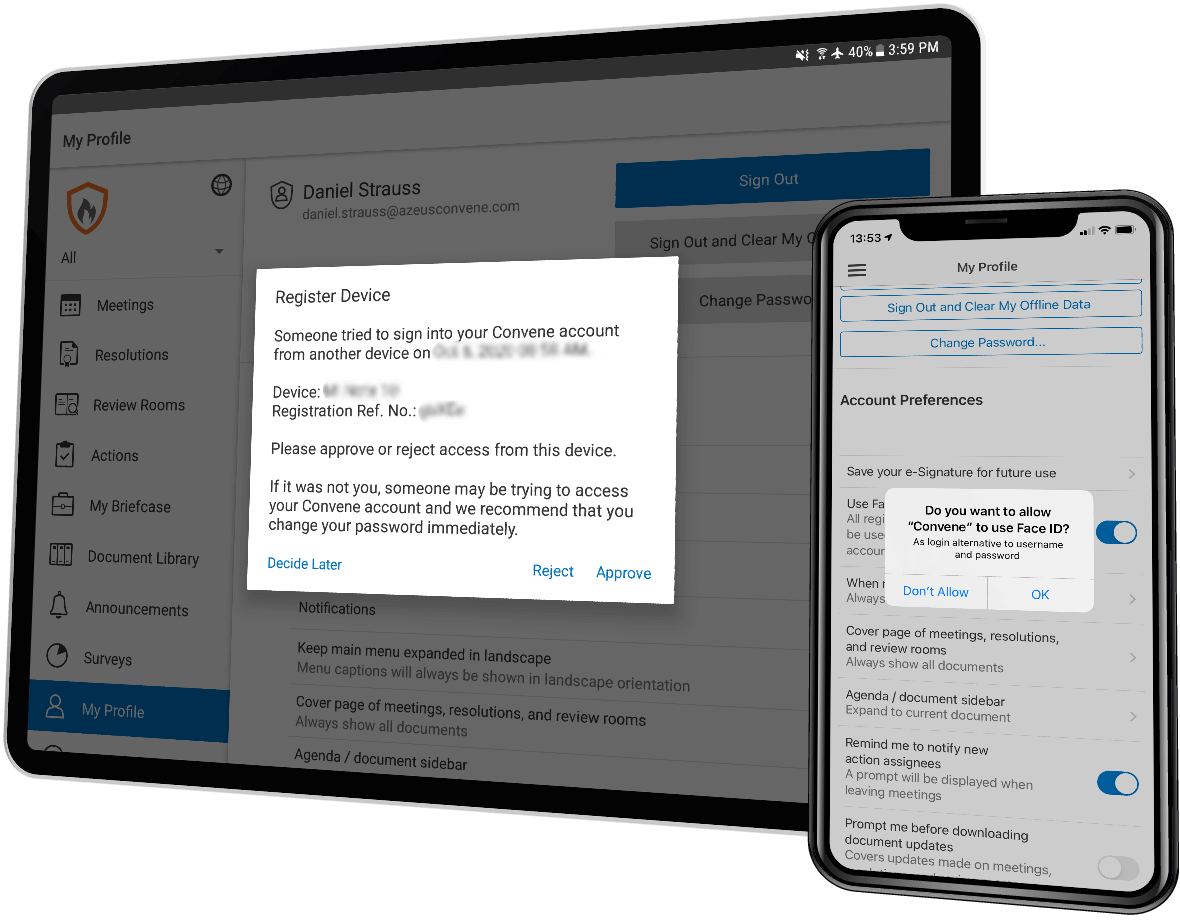
Application Security
Convene grants its users full system ownership—from managing user roles and devices to setting system and security preferences.

Cloud Infrastructure and Network Security
Government-approved cloud hosting, cloud data segregation and availability, 24/7 Intrusion Detection System, 24/7 Intrusion Prevention System, and back-up and recovery.

Security Governance
Convene has defined security policies, a designated security team, GDPR-compliant data processing procedures, business continuity measures, incident detection mechanisms, vulnerability management procedures and personnel security.
Certifications
A Testament to Our Dedication to Security
Satisfied clients including FTSE 100 companies, Fortune 500 companies, banks, and governments in over 100 countries worldwide trust Convene as their secure board portal and meeting solution.
Leading companies choose Convene





Security
Equipped with advanced security features and end-to-end encryption, Convene’s multi-layered approach offers users high levels of data protection, access control, availability, and application security.

Application Security
Convene grants its users full system ownership — from managing user roles and devices to setting system and security preferences. Whether used on a mobile device, tablet, or desktop, Convene and all meeting processes are secure from any threats or vulnerabilities.

Cloud Infrastructure and Network Security
Convene offers government-approved cloud hosting, cloud data segregation and availability, 24/7 Intrusion Detection System, 24/7 Intrusion Prevention System, and back-up and recovery.

Security Governance
Convene has defined security policies, a designated security team, GDPR-compliant data processing procedures, business continuity measures, incident detection mechanisms, vulnerability management procedures and personnel security.
Keeping your data secure is our top priority
Learn how Convene can give your boards a superior meeting experience. Enquire for a free demo with no cost or obligation.