What is a board portal?
A board portal is a secure digital platform for board directors to hold meetings, share confidential information, and execute governance duties. Equipped with collaborative tools, it streamlines the meeting cycle for better decision-making.
Your Meeting Cycle with Board Portal Software
Every board portal solution’s core functionality is to securely solve bottlenecks and redundancies in the meeting process. Here’s what you can expect in implementing one, specifically Convene.
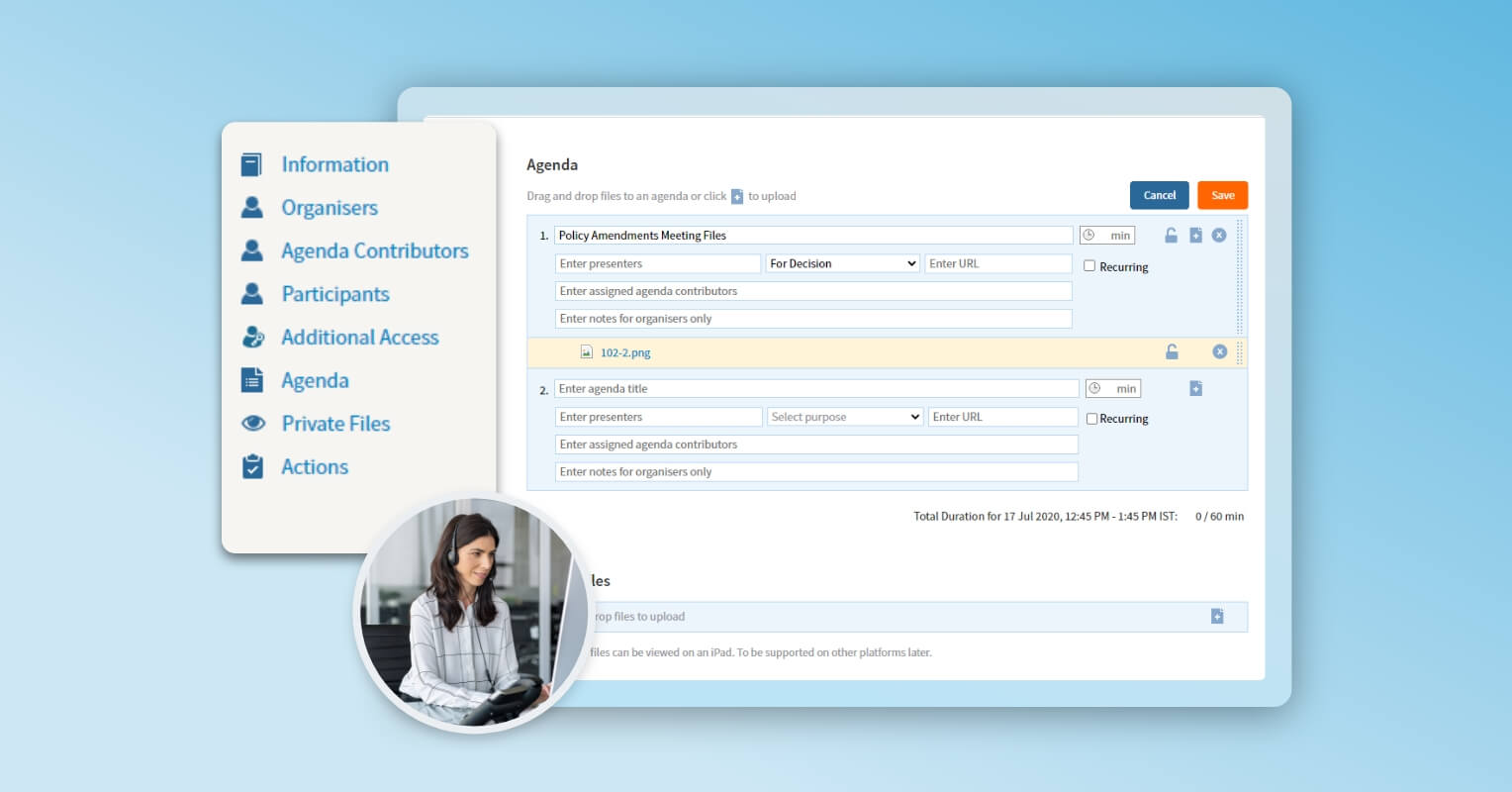
Pre-Meeting
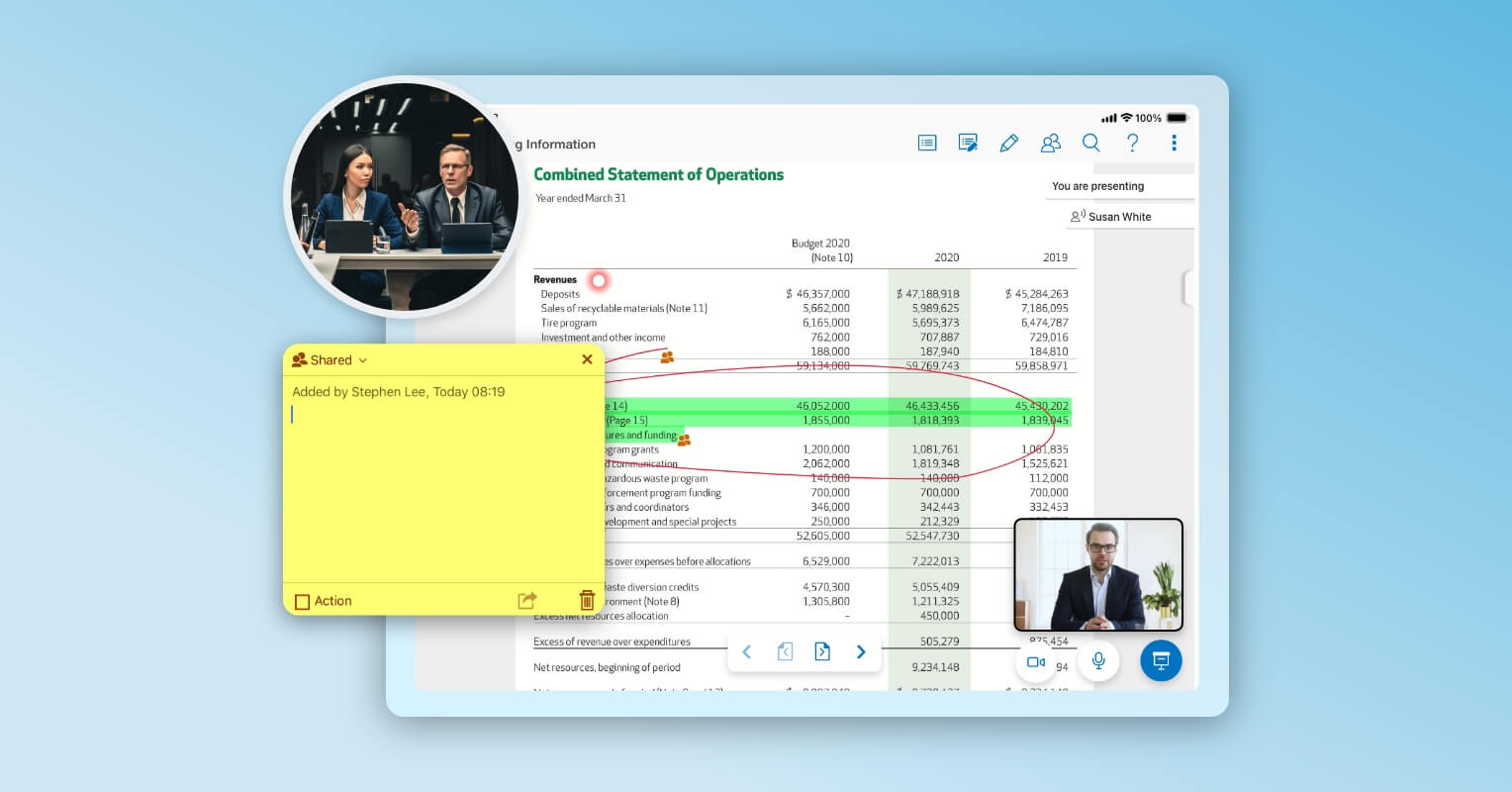
During Meeting
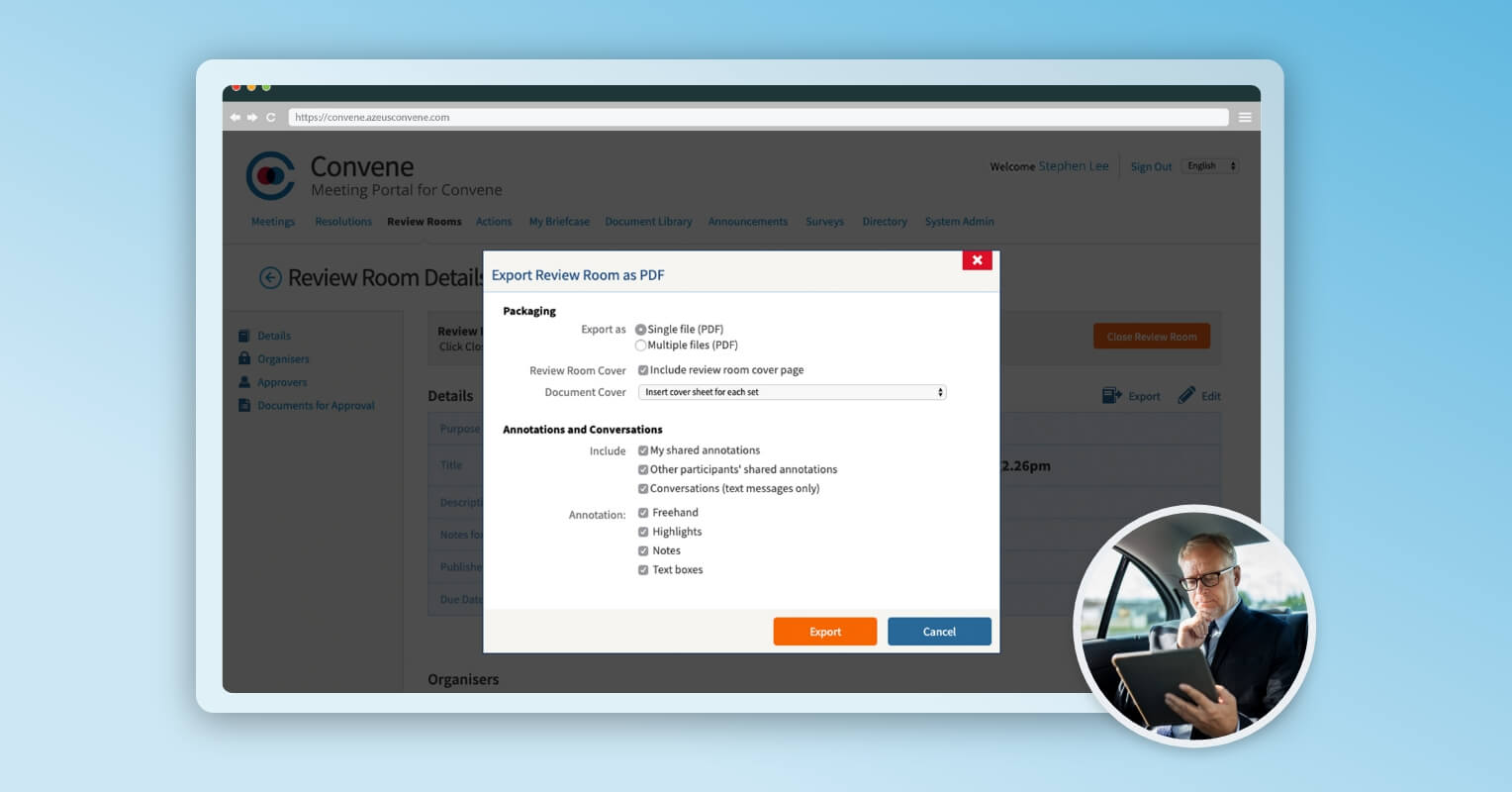
Post-Meeting
Who are the primary users of a board portal?
Convene is built for everyone on board, seamlessly adapting to the needs of leaders, administrators, and everyone in between. Experience next-level ease of use paired with top-tier security — redefining how your board works together.

Board Directors
Stay updated and make informed decisions with an intuitive platform, made for your leadership needs.

CEOs & Executives
Engage in discussions and manage daily operations with Convene’s flexible and accessible board software.

Company Secretaries
Organize meetings while maintaining regulatory compliance with Convene’s world-class security & encryption.

Board Administrators
Simplify board tasks with a centralized document hub and automated notifications and workflows.
What are the benefits of using a board portal?
Engineered to enhance the overall board meeting experience, Convene empowers efficiency and governance across all sectors, including corporations, government, nonprofits, financial institutions, universities, and healthcare.

Improved Communication
Easily share information, collaborate, and communicate with members and directors in real-time, from any location using any device.

Increased Productivity
Spend less time preparing for meetings and stay focused on the agenda. Create meeting packs in just a few clicks, and instantly send out minutes post-meeting.

Better Decision-Making
Easily access reports and documents critical for making informed decisions, aligned with your strategic goals.

Enhanced Strategic Planning
Support your planning and monitoring activities by reviewing, collaborating, and voting on operational data, KPIs, and financial reports — all using the same board software.

Stronger Security
Worry less about cybersecurity. Board portals like Convene implement encryption, firewalls, two-factor authentication, and data backup — ensuring confidentiality and compliance with data privacy laws.

Reduced Costs
Say goodbye to unnecessary expenses with board portals. No need for manual paper files and separate apps to conduct voting, document reviews, and meetings. All you need is one platform.
Must-Have Features for Your Ideal Board Portal
Maximize your investment by finding the right tools that address your needs and perform beyond. To experience efficiency, collaboration, and better governance, look for these electronic board portal features — readily available with Convene.
Take the Next Move
How to Choose the Right Board Portal for Your Organization
Implementing new technology requires a thorough assessment of the capabilities you actually need and those of additional value. This will ensure that your digital investment is worth every penny.
So, what should you consider? Beyond a board portal’s benefits, you should also examine how the platform can support you and the reliability of the vendor available. Below are the key questions you should discuss with your board to determine the right board software for you.

How can a board portal support the efficiency of meetings and board processes?
The right software should promote collaboration and productivity throughout the meeting cycle. You need to ensure that the digital board portal is designed with easy-to-use tools that can hold secure and strategic discussions whenever and wherever your board members are. They should have immediate access to meeting documents and last-minute updates, so they’re ready to partake in fruitful discussions.
Moreso, corporate secretaries can build agenda packs within minutes as every piece of information can be retrieved in a secure centralized repository. Minutes and action items can easily be communicated and tracked by assistants within a board portal software.

Is the board portal easy for board members to use?
For a platform to be adopted and embraced by the board, it should be accessible to members across multiple devices and browsers. Tools don’t have to be complicated. The goal is to provide better functionality without sacrificing convenience. Your directors must be able to navigate and annotate documents on a board portal the way they do with a hard copy.
The right solution must offer intuitive tools accompanied by 24/7 product support and training for users.

How secure should a board portal be?
Security is one of the concerns of boards when going digital, due to data breaches and scams. For industries like financial services that demand enterprise-grade security, it’s crucial to have features such as document encryption, role-based access controls, auto purge capabilities, and robust device security.
Look also for government-approved cloud hosting offerings, enterprise continuity measures, and industry-compliant data processing procedures, such as GDPR.

How is the service and support of the board portal provider?
Is the vendor known in the board management space? Are existing clients satisfied with the service and support of the vendor? Beyond smart tools, a board of directors’ portal is the better choice when its vendor provides tailored customer support at any time.
Check also the vendor’s reviews, awards, and accreditations. These are key indicators of reliability and customer satisfaction. Azeus Convene, for instance, is a CMMI Level 5-accredited company with various awards from authorized review platforms like G2 and Capterra.

What is the return on investment with the board portal?
Besides board portal pricing, part of evaluating your choices is considering what value you can get from what you spend. Look for a solution that can ensure savings in time, paper costs, and even labor. Also, look into how it can support your goals. Can it boost operations for a more agile board? Will it ensure better decision-making and governance outcomes? Will this reduce paper consumption and support sustainability?
The right board software should take you closer to achieving your corporate goals and success.
Frequently Asked Questions About Board Portals
Can board portals be accessed on mobile devices?
Yes! Board portals, such as Convene, are specifically developed to be accessible on a wide range of mobile devices, including smartphones and tablets. They typically provide mobile applications or responsive web interfaces that enable board members to securely access meeting materials, collaborate, and actively participate in board activities while on the move.
Can board portals integrate with other corporate systems?
Integration enables smooth data exchange, streamlines workflows, and enhances productivity by eliminating manual data entry and facilitating information sharing across platforms. Convene can be integrated with videoconferencing platforms such as Zoom and Microsoft Teams, document management systems like DropBox and SharePoint, and signature providers, such as DocuSign, Adobe Sign, and stc.
How long does it take to implement a board portal?
The timeframe for implementing a board portal depends on factors like organizational size, process complexity, and customization needs. However, with effective planning and collaboration with the portal provider, implementation usually takes a few days to a couple of weeks. The process involves portal setup, configuring user permissions, data migration, and providing training to board members and administrators.
How much does a board portal cost?
The cost of a board portal can vary widely depending on several factors. Many providers offer tiered pricing plans based on features, number of users, and storage capacity. Generally, they can cost anywhere from a few hundred dollars to a thousand dollars per month.
Get Started with Convene
See why organizations worldwide are making the switch to board portal for improved board governance. Convene has been rated the top board management software by several trusted sources of technology reviews.